Banner grabbing is the act of getting software banner information (name and version), whether it’s done manually. Or by using any OSINT tools that can do it for you automatically.
This technique can use to grab all the services running on the open ports of that particular system. Banner Grabbing attack is the term used when the hacker is to send a request to the system they are attempting to hack to gain more information and this can cause exploitation of the service, so for the security purpose, if there is no primary need for it then it is removed by the company or the institution.
Definition
Contents
Banner Grabbing is a technique used to gain information about a computer system on a network and the services running on its open ports. Administrators can use this to take inventory of the systems and services on their network.
How Does Banner Grabbing Work?
The attack has three necessary steps. First, the attacker chooses the service he or she wants to target. He or she then launches a request to the target application or system. When the software or device responds, he or she inspects the response to determine what exploit to use for the attack.
Service Ports used During Banner Grabbing
Popular service ports used for banner include:
- Port 80 running HyperText Transfer Protocol (HTTP) service
- Port 21 running File Transfer Protocol (FTP) service
- And Port 25 running the Simple Mail Transfer Protocol (SMTP) service
Banner grabbing techniques
This is the most popular type of banner grabbing. It is basically the act of sending packets to the remote host and waiting for their response to analyze the data.
These techniques involve opening a TCP (Transmission Control Protocol) connection between an origin host and a remote host. It can be considered active, as your connection will be logged in to the remote system. This is the riskiest approach to banner grabbing as it’s often detected by some IDS.
On the other hand, passive banner grabbing enables you to get the same information while avoiding a high level of exposure from the origin connection. Different intermediate software and platforms can be used as a gateway to avoid a direct connection and still allow you to obtain the data you need. Using 3rd party networks tools or services such as search engines, Shodan, or sniffing the traffic to capture and analyze packets, can help you determine software versions.
Commonly used Tools
- Telnet: this classic cross-platform client allows hackers and pen-testers to interact with remote services for banner grabbing. Pen-testers and attackers can telnet to hosts on the default telnet port (TCP port 23) to discover relevant information. Attacks can telnet other commonly used ports like SMTP, HTTP, and POP3. Most operating systems can establish Telnet sessions, allowing users to perform banner grabbing
- Whatweb: the tool recognizes websites, helping hackers and security analysts to grab the web-applications banner by disclosing the server information such as the IP address, version, webpage title, and running operating system
- cURL: the tool has a command that includes the functionality for retrieving banner details from HTTP servers
- Wget: the tool can lead users to remote or local servers’ banner. Wget uses a simple script to suppress the expected output and print the headers sent by the HTTP server
- Netcat: the tool is one of the oldest and popular network utilities for Unix and Linux.
- DMitry: The Deepmagic Information Gathering Tool can gather as much host information as possible. DMitry allows attackers to get all the data from a remote host, including DNS enumeration, subdomain mapping, open ports, and much more.
- Nmap: this simple banner grabber connects to an open TCP port and prints out details sent by the listening service within a few seconds
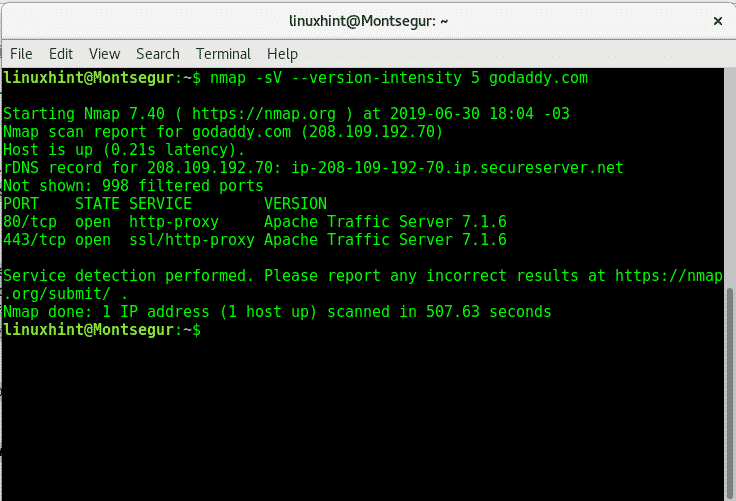
How to Prevent Banner Grabbing ?
- Restrict access to services on the network
- Shut down unused or unnecessary services running on network hosts
- You can override your server’s default banner behavior to hide version information. System administrators can customize default banners, configure the network host’s application or operating system to disable the banners, or remove information from the banners that could give an attacker a leg up.
- Keep your server and systems up to date to secure your applications against known server exploits
CONCLUSION
The technique of banner Grabbing can be used by the authorities to get credential information from some systems and can also be used by non-ethical hackers who would try to invade and steal information from the targeted system for authorities. The former is known as white hat hacking while the latter is called grey hacking. It helps tally the information available on a system by connecting to its host server. The technique is of two types, one is Active Banner Grabbing while the other one is Passive Banner Grabbing. There are several tools available for attempting Banner Grabbing. Few examples of these tools are telnet, cURL, Wget, etc.




1 Comment