[ad_1]

Hi Hackies,
Today I am going to introduce a new thing about hacking ‘OS Command Injection’.
This is also known as shell injection. This is similar to SQL injection.
-<-Lets start the introduction->-
What is OS command injection?
Contents
OS command injection is a web vulnerability that allows an attacker to execute arbitrary operating system (OS) commands on the server that is running an application, and typically fully compromise th application and all its data.
This is very dangerous hack because the hacker can get full control. The attacker change everything ,I mean everything like (credentials, biodata, and also harm the website owner etc.).
What are the types of OS command injection?
I’m not going in deep
- 1.Direct Command Injection
- 2.Indirect Command Injection
- 3.Bling Command Injection
How does OS Command Injection Attack Works?
Firstly the attacker locate a vulnerability in the web application which allow him to execute malicious OS commands.
Usually the attacker make a malicious script or execute commands to bypass the firewall to execute a desired attack in the host OS.
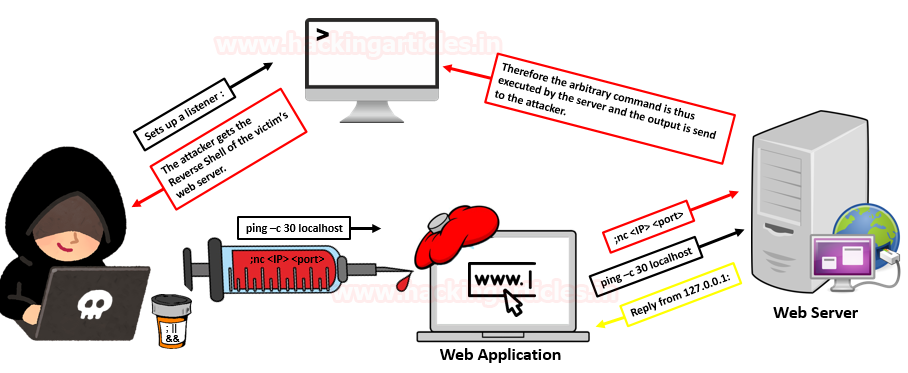
They typically use an input mechanism like HTML code, cookies or form fields to inject this command into the web application.
The browser interprets the command and it is translated to an operating system command on the host machine.
The threat attack can execute specific commands on the host machine and the infected network system.
OS Command Injection ATTACK Example
For this purpose, I am using the ping functionality, whick is notoriosly insecure on many routers. Lets imagine a application which is vulnerable.
It has a comman function that passes a n IP address from a user input is 127.0.0.1.
The following command will be executed on the host OS.
ping -c 5 127.0.0.1Since we are dealing with a vulnerabe web application, it’s possibleto break out the ping command or an error that returns useful info to the attacker.
Then the attacker use this option to execute his own arbitrary commands.
The added additional system commands could look like this:
ping -c 5 127.0.0.1; idIn above command both ping and id command executed.
Command output will looks like :-
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.023 ms64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.074 ms64 bytes from 127.0.0.1: icmp_seq=3 ttl=64 time=0.074 ms64 bytes from 127.0.0.1: icmp_seq=4 ttl=64 time=0.072 ms64 bytes from 127.0.0.1: icmp_seq=5 ttl=64 time=0.037 ms
--- 127.0.0.1 ping statistics ---5 packets transmitted, 5 received, 0% packet loss, time 3999msrtt min/avg/max/mdev = 0.023/0.056/0.074/0.021 msuid=0(root) gid=0(root) groups=0(root)During the OS command injection attack, the attacker can also set up an error-based attack. For ex:-
ping -c 5 "$(id)"The above code returns a response like:-
ping: unknown host uid=0(root) gid=0(root) groups=0(root)How to prevent OS command injection?
To prevent an attacker from exploiting a vulnerable web application and inserting special characters into an operating system command, you should try to generally avoid system calls where possible.
In all cases, avoid user input of any kind unless it is absolutely necessary. If you don’t need system command fucntionality, deactivate it.
Then the attacker can’t get access to the system shell on the host OS through vulnerable web applications. You can also build a whitelist of possile inputs and check the formats.
So good bye. See you next time.
[ad_2]



