Encryption is the method by which information is converted into secret code that hides the information’s true meaning. The science of encrypting and decrypting information is called cryptography.
In computing, unencrypted data is also known as plaintext, and encrypted data is called ciphertext. The formulas used to encode and decode messages are called encryption algorithms, or ciphers.
Purpose of Data Encryption
Contents
The purpose of data encryption is to protect digital data confidentiality as it is stored on computer systems and transmitted using the internet or other computer networks. The outdated data encryption standard (DES) has been replaced by modern encryption algorithms that play a critical role in the security of IT systems and communications.
These algorithms provide confidentiality and drive key security initiatives including authentication, integrity, and non-repudiation. Authentication allows for the verification of a message’s origin, and integrity provides proof that a message’s contents have not changed since it was sent. Additionally, non-repudiation ensures that a message sender cannot deny sending the message.
How does encryption work?
When information or data is shared over the internet, it goes through a series of network devices worldwide, which form part of the public internet. As data travels through the public internet, there is a chance it could be compromised or stolen by hackers. To prevent this, users can install specific software or hardware to ensure the secure transfer of data or information. These processes are known as encryption in network security.
Encryption involves converting human-readable plaintext into incomprehensible text, which is known as ciphertext. Essentially, this means taking readable data and changing it so that it appears random. Encryption involves using a cryptographic key, a set of mathematical values both the sender and recipient agree on. The recipient uses the key to decrypt the data, turning it back into readable plaintext.
The more complex the cryptographic key, the more secure the encryption – because third parties are less likely to decrypt it via brute force attacks (i.e. trying random numbers until the correct combination is guessed).
Encryption is also used to protect passwords. Password encryption methods scramble your password, so it’s unreadable by hackers.
Different Types Of Encryption
As technology is advancing, modern encryption techniques have taken over the outdated ones. Hence, there are several different types of encryption software that have made our job easy. So for your ease, I have provided you with a list of best encryption types below.
Triple DES
It is an advanced version of DES block cipher, which used to have a 56-bit key. However, as the name suggests, TDES encrypts data using a 56-bit key thrice, making it a 168-bit key. It works in three phases when encrypting the data:

- encrypt
- decrypt
- re-encrypt
Likewise, the decryption phases would be:
- decrypt
- encrypt
- decrypt again
Since it encrypts thrice, therefore it is much slower as compared to other types of encryption. Not only that, but it also encrypts data in shorter block lengths, therefore it becomes fairly easy to decrypt the data during the entire encryption process. Hence, there is a higher risk of data theft. However, before other modified types of encryptions emerged, it was the most recommended and widely adopted algorithm.
You probably won’t use DES or even 3DES on your own today. Banking institutions and other businesses may use 3DES internally or for their private transmissions. The industry standard has moved away from it, however, and it’s no longer being incorporated into the newest tech products.
AES
One of the most secure encryption types, Advanced Encryption Standard (AES) is used by governments and security organizations as well as everyday businesses for classified communications. AES uses “symmetric” key encryption. Someone on the receiving end of the data will need a key to decode it.
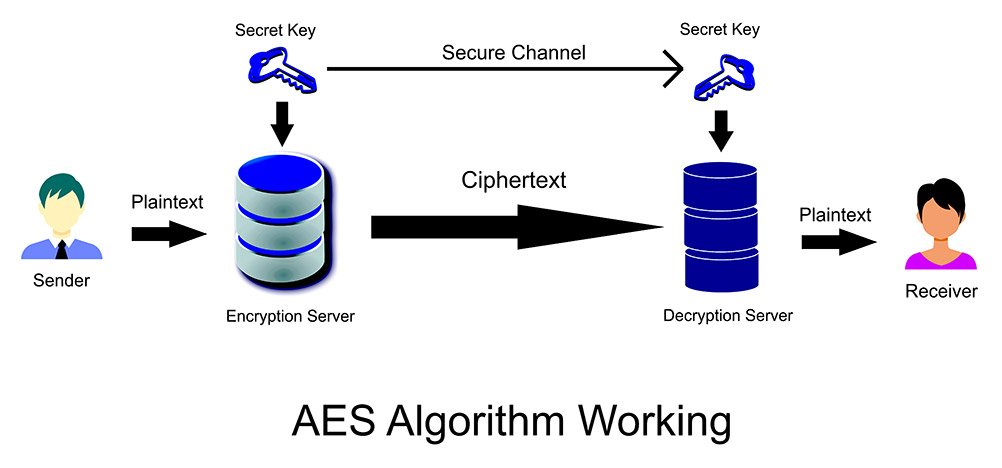
AES differs from other encryption types in that it encrypts data in a single block, instead of as individual bits of data. The block sizes determine the name for each kind of AES encrypted data:
- AES-128 encrypts blocks of a 128-bit size
- AES-192 encrypts blocks of a 192-bit size
- AES-256 encrypts blocks of a 256-bit size
In addition to having different block sizes, each encryption method has a different number of rounds. These rounds are the processes of changing a plaintext piece of data into encrypted data or ciphered text. AES-128, for example, uses 10 rounds, and AES-256 uses 14 rounds.
USE
Most of the data tools available on the market today use AES encryption. Even those that allow you to use other methods with their programs recommend the AES standard. It works in so many applications, and it’s still the most widely accepted and secure encryption method for the price. In fact, you’re probably using it without even knowing it.
RSA Encryption
Another popular encryption standard is “Rivest-Shamir-Adleman” or RSA. It is widely used for data sent online and relies on a public key to encrypt the data. Those on the receiving end of the data will have their own private key to decode the messages. It’s proven to be a secure way to send information between people who may not know each other and want to communicate without compromising their personal or sensitive data.

USE
You’ll need to know a little bit about using RSA to make it part of your routine, but once established, it has many uses. Some people use it to verify a digital signature and ensure the person they are communicating with is really who they say they are. It takes a long time to encrypt data this way, however, and isn’t practical for large or numerous files.
Encryption Applications
1. Hashes
Hash functions provide another type of encryption. Hashing is the transformation of a string of characters into a fixed-length value or key that represents the original string. When data is protected by a cryptographic hash function, even the slightest change to the message can be detected because it will make a big change to the resulting hash.
Hash functions are considered to be a type of one-way encryption because keys are not shared and the information required to reverse the encryption does not exist in the output. To be effective, a hash function should be computationally efficient (easy to calculate), deterministic (reliably produces the same result), preimage-resistant (output does not reveal anything about input) and collision-resistant (extremely unlikely that two instances will produce the same result).
2. Digital Certificates
Once you have identified that your encrypted information is not altered, it is also necessary to identify from which source your encrypted information is coming and who will decrypt it. This is where digital certificates come in, which are also known as identity certificates or public-key certificates.
They authenticate the details of the sender and receiver of the encrypted data over the internet using various types of encryption methods. Any certification authority will issue you your digital certificate. It will contain the following:
- Your name
- Certificate authority’s name
- Unique certificate serial number
- Its expiry date
- Unique private key
- Certificate authority’s digital signature
Once your digital certificate is issued, you can use it as a source of verification for your various online needs.



