What is Phishing ?
Contents
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
The information is then used to access important accounts and can result in identity theft and financial loss.
What is Phishing Attack ?
Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about in order to protect themselves.
What are the different types of phishing attacks?
Phishing attacks can have a great range of targets depending on the attacker. They could be generic phishing emails looking for anyone who has a PayPal account. These are usually recognizable as phishing.
Phishing can go to the other extreme when an email is targeted to one person. The attacker takes great care to craft the email, usually because of the access they have. If the email is at this end of the spectrum, it is very difficult for even the most cautious not to fall prey to it. Statistics show that 91% of information security breaches begin with a phishing scheme of some kind.
What is spear phishing?
Spear phishing targets a specific group or type of individual such as a company’s system administrators. If you are going fishing with a pole, you could pull in an old boot, a tuna, or a flounder – any kind of fish. If you are going fishing with a spear, you are picking a specific fish to go after. Hence the name.
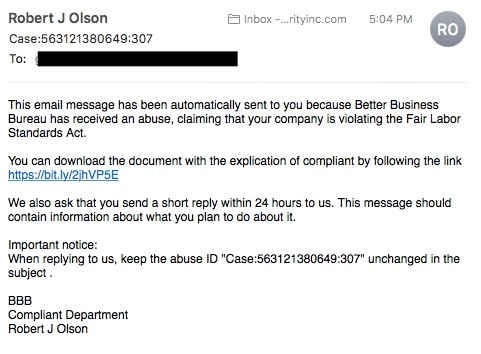
What is whaling?
Whaling is an even more targeted type of phishing as it goes after the whales, the really BIG fish. These attacks target the CEO, CFO, or any Cxx within an industry or a specific business. A whaling email might state that the company is getting sued and you need to click on the link to get more information.
The link takes you to a page where you are asked to enter critical data about the company such as tax ID and bank account numbers. Whaling is an inaccurate name since whales are not actually fish.
What is smishing?
Smishing is an attack that uses text messaging or short message service (SMS) to get your attention. A message that comes into your cell phone through SMS that contains a link to click or a phone number to call could result in a smishing attack.
A scenario that has played out many times is an SMS that looks like it is coming from your bank. It tells you your account has been compromised and you need to respond immediately. The attacker asks you to verify your bank account number, SSN, etc. Just like that the attacker has control of your bank account.

What is vishing?
Vishing carries the same theme as all the other phishing attacks. The attackers are still after your personal information or sensitive corporate information. This attack is accomplished through a voice call. Hence the “v” rather than the “ph” in the name.
A classic vishing attack is the caller who claims to be from Microsoft and says you have a virus on your computer. You turn over credit card details to get a better version of anti-virus software installed on your computer. The attacker now has your credit card information and you have likely installed malware on your computer.
The malware could contain anything from a banking trojan to a bot (short for robot). The banking trojan watches your online activity to steal more details from you – this time your bank account information, including your password.
A bot is a piece of software that will do whatever the hacker wants it to do. It is controlled by command and control (CnC) to mine for bitcoins, send spam, or launch an attack as part of a distributed denial of service (DDoS) attack
What is email phishing?
Email phishing is the most common type of phishing, and it has been in use since the 1990s. Hackers send these emails to any and all email addresses they can obtain. The email usually tells you there has been a compromise to your account and that you need to respond immediately by clicking on a provided link. These attacks are usually easy to spot as the English is not clear. It can seem that someone used a translation program and went through 5 different languages before arriving at English.
Some emails are much harder to recognize as phishing. When the language and grammar are more carefully crafted, the English may not give it away as a phishing email. Checking the email source and the link that you’re being directed to can give you clues as to whether the source is suspicious.
Another phishing scam, referred to as sextortion, occurs when a hacker sends you an email that appears to have come from you. The hacker claims to have access to your email account and your computer. They claim to have your password and a recorded video of you.
The recorded video is where the sextortion part comes in. The hackers claim that you have been watching adult videos from your computer while the camera was on and recording. The demand is that you pay them, usually in bitcoin, or they will release the video to family or colleagues.
Common Features of Phishing Emails
- Too Good To Be True – Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately. For instance, many claim that you have won an iPhone, a lottery, or some other lavish prize. Just don’t click on any suspicious emails. Remember that if it seems to good to be true, it probably is!
- Sense of Urgency – A favorite tactic amongst cybercriminals is to ask you to act fast because the super deals are only for a limited time. Some of them will even tell you that you have only a few minutes to respond. When you come across these kinds of emails, it’s best to just ignore them. Sometimes, they will tell you that your account will be suspended unless you update your personal details immediately. Most reliable organizations give ample time before they terminate an account and they never ask patrons to update personal details over the Internet. When in doubt, visit the source directly rather than clicking a link in an email.
- Hyperlinks – A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different or it could be a popular website with a misspelling, for instance www.bankofarnerica.com – the ‘m’ is actually an ‘r’ and an ‘n’, so look carefully.
- Attachments – If you see an attachment in an email you weren’t expecting or that doesn’t make sense, don’t open it! They often contain payloads like ransomware or other viruses. The only file type that is always safe to click on is a .txt file.
- Unusual Sender – Whether it looks like it’s from someone you don’t know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general don’t click on it!
What is search engine phishing?
Search engine phishing, also known as SEO poisoning or SEO trojans, is where hackers work to become the top hit on a search using google or other engines. If they can get you to click on their link, it takes you to the hacker’s website. When you interact with it and enter sensitive data, they have your information. Hacker sites can pose as any type of website, but the prime candidates are banks, PayPal, social media and shopping sites.
How does phishing work?
Phishing starts with a fraudulent email or other communication that is designed to lure a victim. The message is made to look as though it comes from a trusted sender. If it fools the victim, he or she is coaxed into providing confidential information, often on a scam website. Sometimes malware is also downloaded onto the target’s computer.
What are the dangers of phishing attacks?
Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain employee login information or other details for use in an advanced attack against a specific company. Cybercrime attacks such as advanced persistent threats (APTs) and ransomware often start with phishing.
How do I protect against phishing attacks?
Though hackers are constantly coming up with new techniques, there are some things that you can do to protect yourself and your organization:
- To protect against spam mails, spam filters can be used. Generally, the filters assess the origin of the message, the software used to send the message, and the appearance of the message to determine if it’s spam. Occasionally, spam filters may even block emails from legitimate sources, so it isn’t always 100% accurate.
- The browser settings should be changed to prevent fraudulent websites from opening. Browsers keep a list of fake websites and when you try to access the website, the address is blocked or an alert message is shown. The settings of the browser should only allow reliable websites to open up.
- Many websites require users to enter login information while the user image is displayed. This type of system may be open to security attacks. One way to ensure security is to change passwords on a regular basis, and never use the same password for multiple accounts. It’s also a good idea for websites to use a CAPTCHA system for added security.
- Banks and financial organizations use monitoring systems to prevent phishing. Individuals can report phishing to industry groups where legal actions can be taken against these fraudulent websites. Organizations should provide security awareness training to employees to recognize the risks.
- Changes in browsing habits are required to prevent phishing. If verification is required, always contact the company personally before entering any details online.
- If there is a link in an email, hover over the URL first. Secure websites with a valid Secure Socket Layer (SSL) certificate begin with “https”. Eventually all sites will be required to have a valid SSL.
Phishing attack examples
The following illustrates a common phishing scam attempt:
- A spoofed email ostensibly from myuniversity.edu is mass-distributed to as many faculty members as possible.
- The email claims that the user’s password is about to expire. Instructions are given to go to myuniversity.edu/renewal to renew their password within 24 hours.

Several things can occur by clicking the link. For example:
- The user is redirected to myuniversity.edurenewal.com, a bogus page appearing exactly like the real renewal page, where both new and existing passwords are requested. The attacker, monitoring the page, hijacks the original password to gain access to secured areas on the university network.
- The user is sent to the actual password renewal page. However, while being redirected, a malicious script activates in the background to hijack the user’s session cookie. This results in a reflected XSS attack, giving the perpetrator privileged access to the university network.
Phishing techniques
Email phishing scams
- Email phishing is a numbers game. An attacker sending out thousands of fraudulent messages can net significant information and sums of money, even if only a small percentage of recipients fall for the scam. As seen above, there are some techniques attackers use to increase their success rates.
- For one, they will go to great lengths in designing phishing messages to mimic actual emails from a spoofed organization. Using the same phrasing, typefaces, logos, and signatures makes the messages appear legitimate.
- In addition, attackers will usually try to push users into action by creating a sense of urgency. For example, as previously shown, an email could threaten account expiration and place the recipient on a timer. Applying such pressure causes the user to be less diligent and more prone to error.
- Lastly, links inside messages resemble their legitimate counterparts, but typically have a misspelled domain name or extra subdomains. In the above example, the myuniversity.edu/renewal URL was changed to myuniversity.edurenewal.com. Similarities between the two addresses offer the impression of a secure link, making the recipient less aware that an attack is taking place.

Spear phishing
Spear phishing targets a specific person or enterprise, as opposed to random application users. It’s a more in-depth version of phishing that requires special knowledge about an organization, including its power structure.
An attack might play out as follows:
- A perpetrator researches names of employees within an organization’s marketing department and gains access to the latest project invoices.
- Posing as the marketing director, the attacker emails a departmental project manager (PM) using a subject line that reads, Updated invoice for Q3 campaigns. The text, style, and included logo duplicate the organization’s standard email template.
- A link in the email redirects to a password-protected internal document, which is in actuality a spoofed version of a stolen invoice.
- The PM is requested to log in to view the document. The attacker steals his credentials, gaining full access to sensitive areas within the organization’s network.
By providing an attacker with valid login credentials, spear phishing is an effective method for executing the first stage of an APT.
How to prevent phishing
Phishing attack protection requires steps be taken by both users and enterprises.
For users, vigilance is key. A spoofed message often contains subtle mistakes that expose its true identity. These can include spelling mistakes or changes to domain names, as seen in the earlier URL example. Users should also stop and think about why they’re even receiving such an email.
For enterprises, a number of steps can be taken to mitigate both phishing and spear phishing attacks:
- Two-factor authentication (2FA) is the most effective method for countering phishing attacks, as it adds an extra verification layer when logging in to sensitive applications. 2FA relies on users having two things: something they know, such as a password and user name, and something they have, such as their smartphones. Even when employees are compromised, 2FA prevents the use of their compromised credentials, since these alone are insufficient to gain entry.
- In addition to using 2FA, organizations should enforce strict password management policies. For example, employees should be required to frequently change their passwords and to not be allowed to reuse a password for multiple applications.
- Educational campaigns can also help diminish the threat of phishing attacks by enforcing secure practices, such as not clicking on external email links.



